Lecture 2.5: Putting it all together
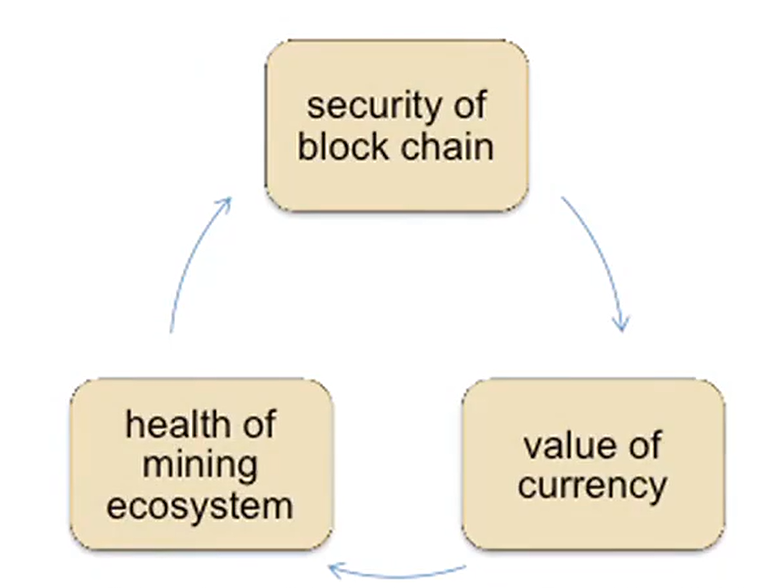
Mining economics
If mining reward > hardware + electricity cost -> Profit
Complications:
- fixed vs. variable costs
- reward depends on global hash rate
Recap
Identities
Transactions
P2P network
Block chain & consensus
Hash puzzles & mining
Bitcoin is bootstrapped
What can a “51% attacker” do?
Steal coins from existing address?
A 51% attatker creates an invalid block that contains an invaild transaction, that represents stealing Bitcoins from an existing address that the attacker doesn’t control and transfering them to his own address. Now this attacker can pretend that that’s a valid transaction, and pretend that’s a valid block and keep building upon this block. And even succeed in making that the longest branch, but the other honest nodes are simply not going to accept this invalid block and are going to keep mining based on the last valid block that they found at the network. So what will happen is that there will be a fork in the chain. Now if the attacker tries to spend these invaild coins, and send them to someone else, and the node may say, “oh, this might be the longest branch but it’s not a valid branch” (because it contains an invalid transaction, because the crypto, the signatures, didn’t check out).
(impossible)
Suppress some transactions?
- From the block chain(possible)
- From the P2P network(impossible)
Because peer-to-peer network doesn’t depend on the block chain, doesn’t depend on consensus.
Change the block reward?
Because the attacker doesn’t control the copies of the Bitcoin software that all of the honest nodes are running. (impossible)
Destroy confidence in Bitcoin.
(possible)